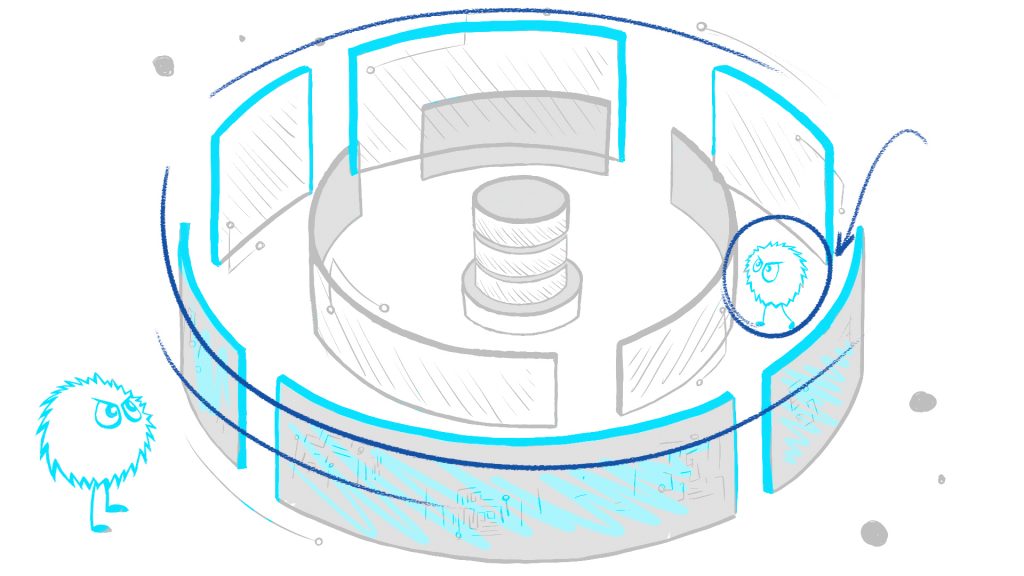
Problem: Permeable Perimeter
It’s impossible to prevent bad actors from penetrating the corporate network because:
- Internal threat – some malicious individuals are already inside your perimeter.
- Social engineering – people make mistakes. No matter how well you train them, someone will click on the wrong email.
- Statistical defenses – Antispam, Antivirus, BYOD, Physical security, and more, can only reduce the number of successful attacks, not stop them all.
One way or another, it is highly likely that a bad actor is already inside your perimeter.
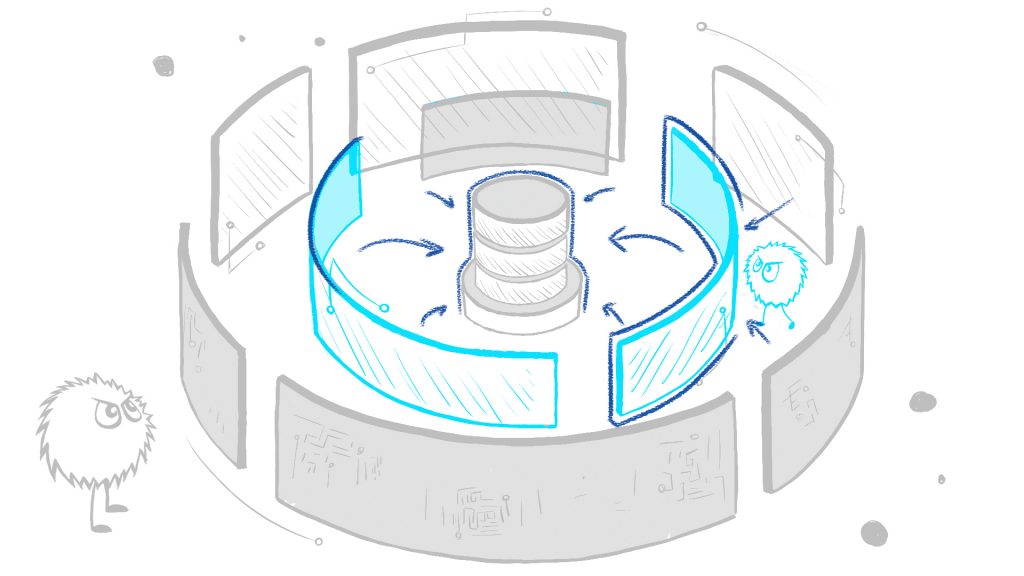
Solution: Data-Centric Defense
With bad actors inside your perimeter, the only way to avoid a data breach is by protecting the data:
- Database defense – protect access to sensitive information. All data breaches must use the database to access the data.
- Application protection – defends the main path to the data. Many data breaches exploit the application.
- Data masking – eliminate risks outside of production. Insecure test and development systems should not contain sensitive data.
Building tight defenses around the data will exponentially reduce the risk of a data breach.
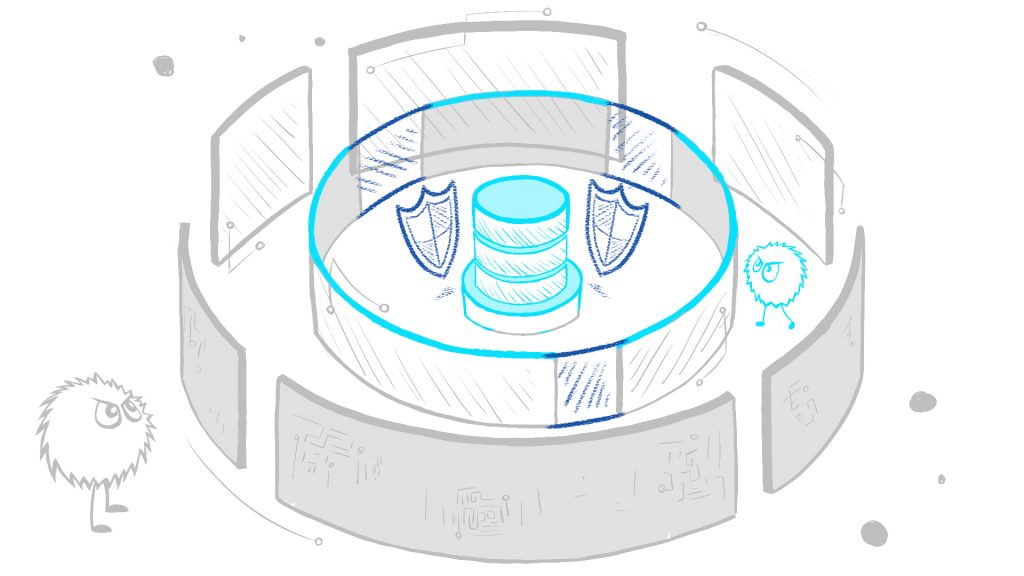
Challenge: Airtight Control
Saying “let’s protect the data” is easy, but creating airtight controls on production systems that run billions of legitimate activities is challenging. How can you find the needle in this enormous haystack?
- Capture, Processing, and Storage – first, you need technology to capture all the activity with negligible overhead, process it efficiently, and store a lot with modest resources. You can’t find a needle you can’t see.
- Visibility & Forensics – control starts with visibility. You need to know what’s happening in your environment. You can’t secure what you don’t understand.
- Analysis & Anomalies – automation is crucial to pinpoint that elusive needle. It is impossible to review billions of activities manually.
- Advanced Prevention – automatically blocks certain activities to reduce your attack surface. Block what you can and detect the rest.
We designed the Core Audit Suite to bring you all this, data masking, and much more. A single, integrated solution that contains all the technology you need to protect your databases and applications, mitigate threats, and respond to attacks.
