Risk Calculator
Estimate the risk of a data breach in your organization. By providing some information specific to your organization you will get an immediate estimate of the risks you are facing.
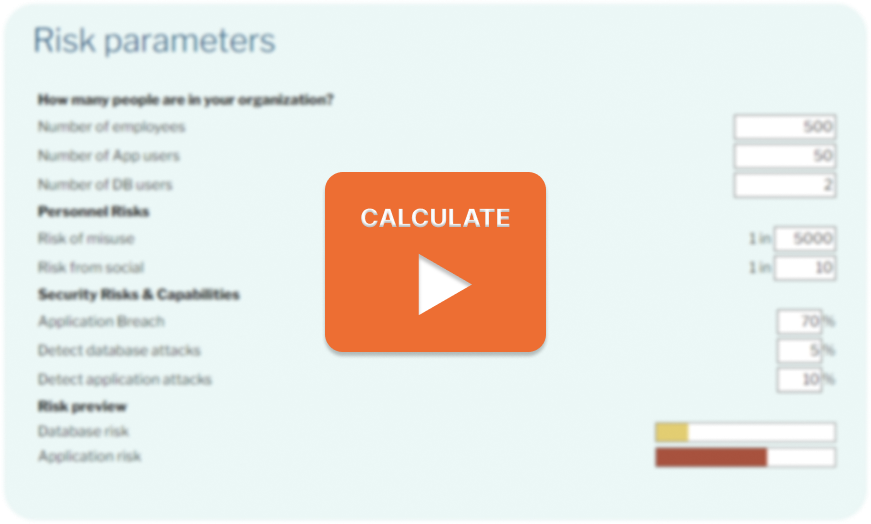
Risk parameters
| How many people are in your organization? | ||
| Number of employees | Enter the number of employees in your company. Or, more accurately, the number of people with access to internal company resources such as the network, email, and active directory. | |
| Number of App users | Enter the number of employees who have access to applications with sensitive information. They don’t necessarily need access to the data but to the applications that contain it. | |
| Number of DB users | Enter the number of employees with direct database access, including DBAs. Or, more accurately, the number of individuals whose database accounts will allow an attacker to steal data. | |
| Personnel Risks | ||
| Risk of misuse | 1 in | What’s the likelihood an employee will try to steal data? This question relates to human nature and the type of employees in your organization. It’s hard to provide reliable estimates, but statistically, 20% of data breaches are from internal threats. There are also estimates that every year, over 20% of companies experience incidents from intentional employee abuse of privilege. We estimate that 1 in 5,000 is a conservative number. |
| Risk from social | 1 in | What’s the likelihood an employee will click on the wrong email and compromise their computer? This risk depends on the type of employees and the amount of training they receive. Companies that perform employee training claim to reduce this risk from 60% to 10%. We, therefore, believe that 1 in 10 (10%) is a conservative estimate. |
| Security Risks & Capabilities | ||
| Application Breach | % | What’s the likelihood that a hacker with access to an application account could steal data? That includes vulnerabilities like SQL injection and the risk the compromised user already has access to the data. |
| Detect database attacks | % | How likely are you to know when an individual uses a database account to steal data? You can estimate this based on the number of false positives you regularly get from your detective/alert systems. Not getting false positives means you are unlikely to know when an attack occurs. |
| Detect application attacks | % | How likely are you to know when an individual uses an application account to steal data or perform an attack? You can estimate this based on the number of false positives you regularly get from your detective/alert systems. Not getting false positives means you are unlikely to get an alert when an attack occurs. |
| Risk preview | ||
| Database risk | Preview of the total database risk. Click View Results for more details. | |
| Application risk | Preview of the total application risk. Click View Results for more details. | |
What does it mean?
help
Risk results
| Threat from employee misuse | The likelihood that an employee (not a DB or App user) will attempt to steal data. | ||
| Threat from employees from social | The likelihood that an employee (not a DB or App user) will fall prey to a social engineering attack. | ||
| Threat from user misuse | The likelihood that one of the application users will attempt to steal data. | ||
| Threat from users from social | The likelihood that one of the application users will fall prey to a social engineering attack. | ||
| Threat to DB from misuse | The likelihood that one of the database users will attempt to steal data. | ||
| Threat to DB from social | The likelihood that one of the database users will fall prey to a social engineering attack. | ||
| Perimeter breach | The likelihood that an individual inside the network (behind the perimeter) will attempt to steal data due to either misuse or social engineering. To intuitively understand this number, consider the number of employees and the social risk from each one. | ||
| Indirect risk | The risk from employees with no application or database access (through misuse or social engineering). This risk is harder to materialize because the attacker must also compromise an application or database account. It’s usually feasible once inside the perimeter but requires an additional step to get to a data breach. | ||
| Direct database risk | The likelihood that data will be stolen from the database directly (through misuse or social engineering). It shouldn’t be over 5-10%. | ||
| Direct application risk | The likelihood that data will be stolen through the application. (through misuse or social engineering). It shouldn’t be over 5-10%. |
Enter your email for a report with customized recommendations:
Contact us with any questions or comments. We’d love to hear from you!
What does it mean?
help
Your database or application risk is over 50%. You’re an easy target waiting to fall prey. There’s a reasonable chance you’ll have a data breach this year or next year if you haven’t already had one you’re unaware of.
Your database or application risk is 20%-50%. There’s a reasonable chance you’ll have a data breach in the next five years because your exposure is statistically high. It’s a question of being targeted or unlucky to fall into the wrong spam campaign rather than your ability to defend.
Your database or application risk is 10%-20%. You have minimal defensive capabilities. There’s a 50/50 chance you’ll have a data breach in the next seven years. Your exposure is moderate, and you’re doing a good job, but you should improve it.
Congratulations! Your database and application risk is lower than 10%, which means you have defensive capabilities and can withstand an attack. If below 5%, you have strong defenses. It doesn’t mean you won’t have a breach, but it’s less likely. Whether from internal abuse or a successful spam campaign, attackers are likely be detected, and your security team can foil the attack.